Explore Snowflake Security Best Practices: A Comprehensive Guide
Ensuring robust security for businesses’ cloud-based data platform is crucial. When it comes to Snowflake, a leading cloud data warehousing solution, implementing effective security measures is vital. Understanding and adhering to Snowflake security best practices can safeguard a company’s sensitive information, prevent unauthorized access, and ensure compliance with regulatory standards. This blog will explore essential strategies and guidelines to help businesses protect data assets and optimize performance and usability.
Let’s discuss the major aspects of Snowflake security:
- Authentication
- SSO (Single Sign-On)
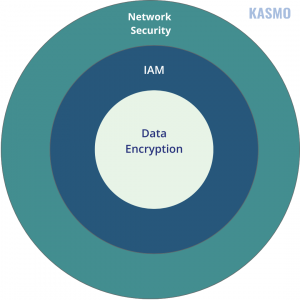
- Network Security
- Data Security
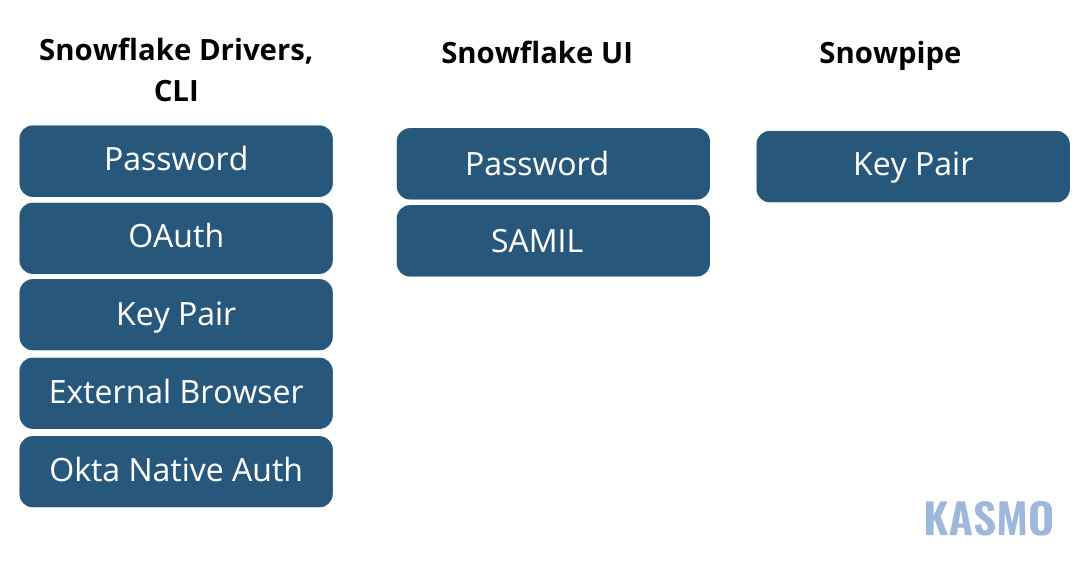
Authentication
Password Protection
Think of your password as the key to your castle. Ensure its strong, complex, and regularly updated. Avoid easily guessable passwords like birthdays or pet names.
Multi-Factor Authentication (MFA)
MFA is like a two-step verification. It adds an extra layer of security, making it much harder for unauthorized access. Only you and your device know the combination.
SAML, OAuth, Key Pair Authentication
- SAML: It’s like a diplomatic passport. It allows you to securely share information between different systems.
- OAuth: Like a tourist visa, it grants temporary access to your data without sharing your password.
- Key Pair Authentication: It uses a pair of cryptographic keys to verify your identity, much like a secret key.
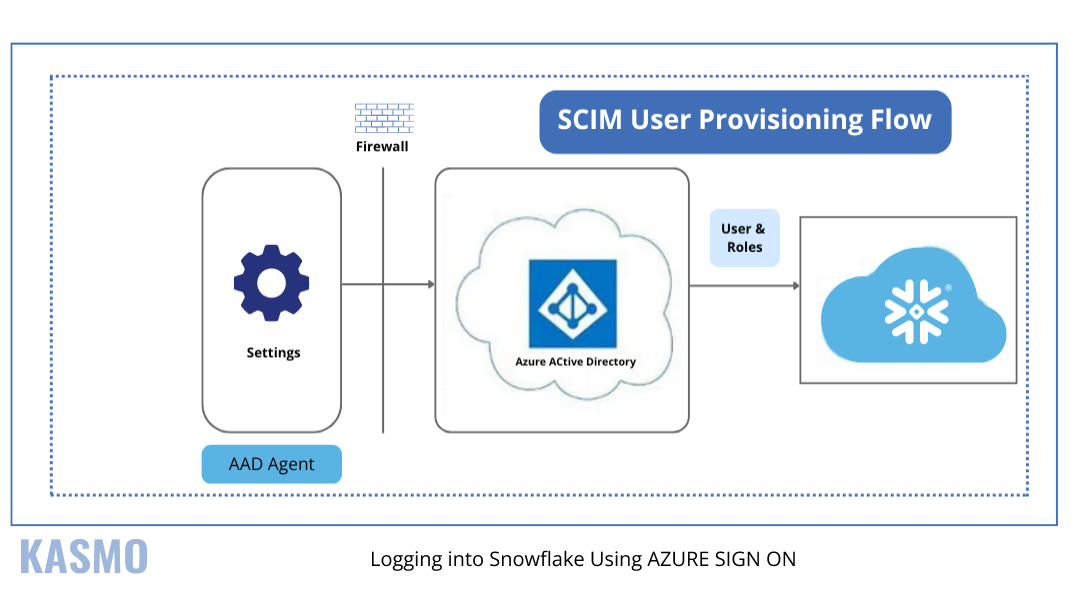
Federated Environment and SSO: Streamlined and Secure Access
One of the key points of Snowflake security best practices is a federated environment that allows you to access multiple systems and applications through a single set of credentials.
Federated Authentication
Integrates with external identity providers to streamline authentication across various platforms.
Single Sign-On (SSO)
Enhances user convenience by enabling access to multiple applications with one set of credentials. This reduces password fatigue and improves security by centralizing authentication management.
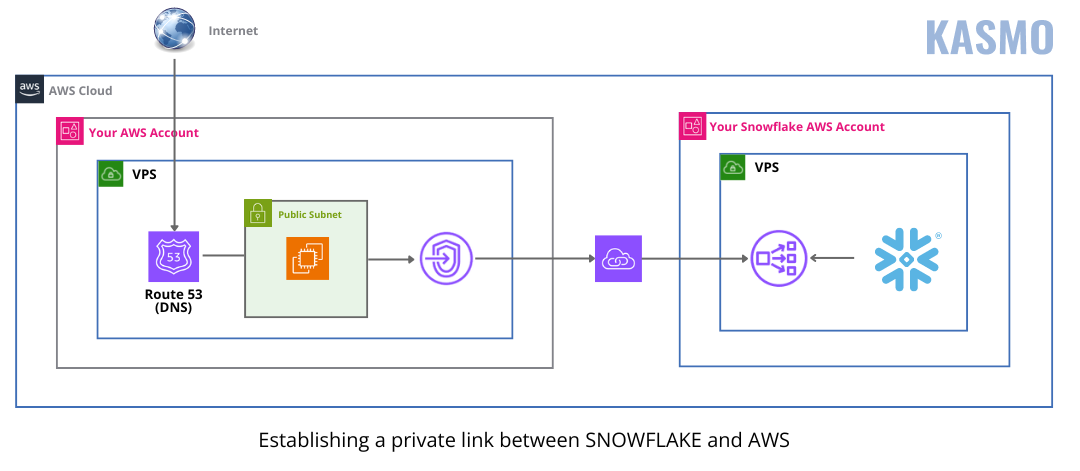
Network Security: Protecting Your Perimeter
Network security ensures that only authorized individuals and systems can access your Snowflake environment.
Network Policies
Establish stringent network policies to control access to Snowflake. This includes limiting IP addresses, defining allowed protocols, and implementing firewall rules.
Private Link
Consider using Snowflake’s private link feature to establish a secure, private connection between your network and Snowflake.
Virtual Private Cloud (VPC)
If applicable, leverage VPCs to isolate your Snowflake environment from the broader public internet.
Data Security
Your data is the most important aspect of your business. Safeguarding it requires a multi-layered approach.
Data Masking
Disguise sensitive information, like hiding a treasure map in plain sight. Data masking protects your data without compromising its utility.
Row-Level Security (RLS)
Create invisible barriers within your castle, restricting access to specific areas based on user roles and permissions.
Access Controls
Assign roles and responsibilities like a well-organized royal court. Role-Based Access Control (RBAC) ensures only authorized individuals can access specific data.
Data Encryption
Lock your data with a strong encryption key. This safeguards your data both when it’s at rest and in transit.
Key Management
Protect the key to your data with utmost care. Proper key management is crucial for maintaining data confidentiality.
By combining these Snowflake security measures, you can protect your data against any cybersecurity threat.
Conclusion
Prioritizing these Snowflake security best practices is essential for safeguarding your cloud data environment. By adopting these Snowflake security measures, you can effectively manage risks, ensure data integrity, and maintain compliance with industry regulations. Implementing robust security measures not only protects your sensitive information but also enhances overall system performance and user confidence. As you continue to leverage Snowflake’s powerful capabilities, keeping these security practices at the forefront will help you achieve a secure and resilient data infrastructure. Talk to us!



